Difference Between Phishing, Smishing, and Vishing
Phishing campaigns primarily target email users across all platforms and rely heavily on sophisticated fake websites that closely mimic legitimate ones, combined with advanced email spoofing techniques that make the messages appear authentic and trustworthy to recipients.
Phishing stands as the most prevalent and widespread type of cyber scam in today's digital landscape, where malicious attackers systematically send fraudulent and deceptive emails while pretending to represent trusted and legitimate organizations such as major banks, government offices, tax authorities, or popular websites and online platforms.
These carefully crafted emails typically contain urgent and alarming messages designed to create panic, such as warnings about immediate account suspension, unusual activity detected, security alerts requiring immediate attention, or verification requests that demand quick action. The emails strategically include malicious links that redirect to fake websites or dangerous attachments containing malware.
When unsuspecting victims click on these deceptive links and unknowingly enter their sensitive personal details, login credentials, financial information, or other confidential data, the attacker successfully captures and steals this valuable information for fraudulent purposes.
Phishing campaigns primarily target email users across all platforms and rely heavily on sophisticated fake websites that closely mimic legitimate ones, combined with advanced email spoofing techniques that make the messages appear authentic and trustworthy to recipients.
Smishing represents a dangerous and increasingly common form of phishing that specifically uses SMS text messages or popular messaging applications instead of traditional email as its primary attack vector.
Unsuspecting victims receive seemingly legitimate text messages that falsely claim to be from well-known courier and delivery services, established banks and financial institutions, telecom providers and mobile operators, or exciting prize campaigns and lottery winnings.
These deceptive messages frequently include shortened or disguised links that hide the true destination URL, or they directly request users to reply immediately with personal information, banking details, passwords, or verification codes.
Smishing has proven to be particularly dangerous and effective because people generally tend to trust text messages significantly more than emails, viewing them as more personal and secure, and they often open and read these messages quickly without taking time for proper verification or careful examination of the sender's authenticity.
Vishing, commonly known as voice phishing or telephone fraud, involves direct phone calls as the primary method of attack and deception. Skilled attackers and social engineers call their targeted victims while convincingly pretending to be legitimate bank officials, authorized customer support agents, law enforcement police officers, tax department representatives, or other trusted government representatives and authority figures.
They skillfully use psychological tactics including fear, urgency, authority, and intimidation to effectively pressure and manipulate victims into immediately sharing highly sensitive information such as one-time passwords (OTPs), complete credit or debit card numbers with CVV codes, account login credentials, social security numbers, or other confidential personal and financial details.
Unlike phishing and smishing which rely on written digital communication, vishing depends entirely on direct human interaction, real-time conversation manipulation, and persuasive voice communication that can be adapted instantly based on the victim's responses and level of trust.
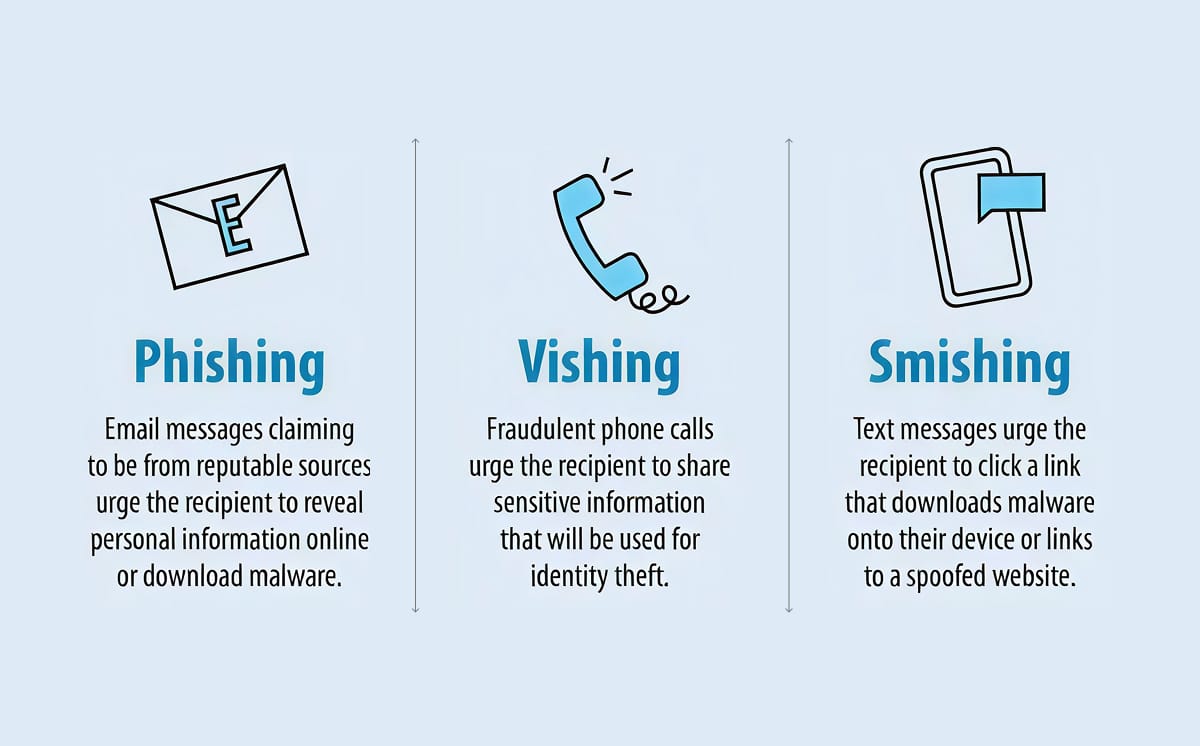
The key and fundamental difference between phishing, smishing, and vishing lies primarily in the specific communication channel and medium employed for the attack.
Phishing exclusively uses email and electronic mail systems, smishing specifically relies on SMS text messages or mobile messaging applications and platforms, and vishing distinctly uses voice calls and telephone conversations as the primary attack method.
However, despite these differences in delivery mechanisms and communication channels, the ultimate goal and objective of all three attack types remains exactly the same: to successfully steal sensitive personal and financial information, compromise security, and gain unauthorized access by strategically exploiting human trust, manipulating emotions like fear and urgency, and taking advantage of people's natural tendency to help or comply with authority figures.
Understanding and recognizing these critical differences and distinct characteristics helps both individuals and businesses identify potential threats more quickly and accurately, respond more appropriately and effectively to suspicious communications, and implement better security measures and protective protocols.
Staying constantly alert, maintaining healthy skepticism, and practicing vigilance across all communication channels including email, text messages, and phone calls is absolutely essential and non-negotiable in today's threat landscape, especially because sophisticated cybercriminals and organized fraud rings often strategically combine and coordinate these different methods in multi-channel attacks to significantly increase their overall chances of success and maximize the number of victims they can compromise.





